 Jason Parekh (jparekh@cc.gatech.edu) Samir Batta (samir@cc.gatech.edu) | ||||||||||||||||||
|
Motivation The Internet proves to be successful network for exchanging content between users, however most applications supporting exchange (web servers, FTP servers, etc.) require a typical client-server set up. Peer-to-peer networks alleviate the difficulties inherent with client-server paradigms: IP addresses, port numbers, firewalls, server installation, separate client/server applications, etc. A typical peer-to-peer application allows a user to share files automatically with all other users running the application enabling an average Internet user to easily exchange content. Sharing of files easily among users becomes more useful as modern technology allows average Internet users to author their own content. Whether it be pictures or a video clip from a recent trip or a weekly podcast, users want to share data with their friends across the Internet. Doing such is tedious-either the user would have to setup his own FTP server or upload pictures to an online photo album. However, with peer-to-peer networks, a user could simply select which directory holds his pictures and videos and any files in that directory are automatically shared. The case also holds when new pictures are transferred from a camera—there will be no need to upload these additions to an online album. This simplicity allows peer-to-peer networks to excel over traditional sharing methods for personalized content. However, since this content is personalized, it should the user's decision whether to share it with the entire network or not. At the moment, peer-to-peer networks do not have a mechanism to limit access for different peers. The only access control method a user has is either allowing a file to be shared, or not. Our approach extends the Gnutella protocol with a simple access control mechanism allowing for variability in the restrictions of shares. A peer is able to annotate access restrictions to each of his shares using privileges such as searchable, viewable, and downloadable for a given set of friends. Starting with these as a base, we will discover other applicable restrictions as we extend our research. Another important consideration is to maintain anonymity in the peer-to-peer network. By enforcing access control, the peer-to-peer network must have some way of identifying peers, however this becomes troublesome as a primary goal of some peer-to-peer networks is to maintain anonymity. We will discover the gradient between the trade-off of anonymity and strong access control in our project. We demonstrate the usefulness of such restrictions with a photo sharing prototype called Photoshare. Photoshare allows a peer to share pictures on an existing peer-to-peer network but allows for fine-grained sharing restrictions through our access control mechanism. Our Previous Work Prior to this project, we have implemented a simple access control mechanism into the Gnutella network. The access control mechanism is a proof-of-concept showing the possibility of such a mechanism built into an already deployed peer-to-peer network spanning thousands of users. The previous project is divided into two components: a backend capable of restricting access to shares, and a graphical user interface capable of modifying access restrictions. The backend extends the LimeWire backend by implementing a set of access control primitives: searchable and downloadable. These primitives are able to be applied to any share, whether a file or directory, and restrict access to any set of users. In order to facilitate the concept of a user in the Gnutella peer-to-peer network, we introduced a unique identifier per peer, which is based on a simple e-mail address. (Note: this method is a quick hack, it is not meant to be used as a true unique identifier as 1) it is extremely easy to alter and 2) it has no notion of anonymity.) The identifier passed along each search/download request by the GGEP--Gnutella Generic Extension Protocol, meaning even peers that do not understand the access control (ie: those that do not run our software) will pass it along. The user interface was designed from scratch to allow for easily controlling shares, friends, and access restrictions. Proposed Work We will extend the previous work to a fully-functional application (Photoshare) demonstrating the usefulness of access control in peer-to-peer networks. This demo application will be capable of allowing users to share pictures and just as easily search across the entire network for pictures from friends or random peers. The demo application will utilize SWT and will focus on simplicity of usage. Therefore, setting permissions and adding groups should be intuitive yet at the same time powerful. We will borrow ideas from social online communities (tagging) and also file systems (access restrictions). Photoshare will require us to create a strong access control model, which is another extension from our previous work. We will explore the area of access control, in terms of both the actual mechanism used in the peer-to-peer network for enforcing it, and which privileges make sense in a peer-to-peer scenario. Although our research will focus mainly in the realm of file-sharing, the notion of access control can be applied to other peer-to-peer applications. Our current ideas for access control are either enforcing access restrictions on the peer who shares content, or enforcing access restrictions on each of the peers along the path from the peer who searches and the peer who shares. The first method will allow for stronger access control but will require a unique identifier for the searching peer to be tagged along each request. The second method instead relies on passing the access control table along with search results and requiring peers on the path to enforce the access. This does not necessarily require the unique identifer, allowing the access control mechanism to have a stronger sense of anonymity, but will have issues in terms of strength (it will be easier an adversary to gain access to files she should be restricted from). 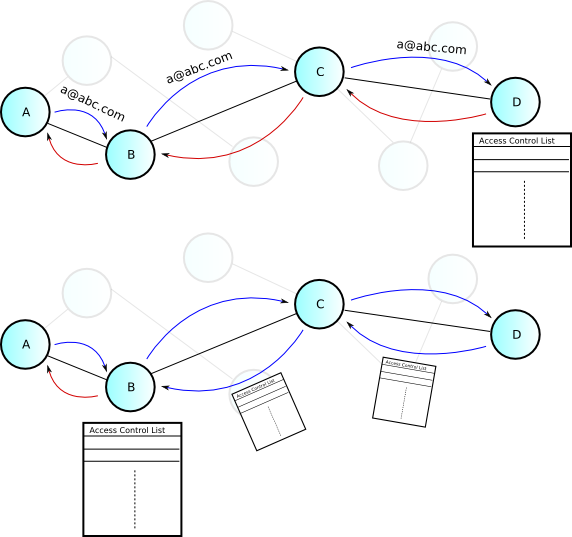 These two scenarios show peer A attempting to download a file from peer D. The top diagram reflects the scenario where a unique identifier (in this case a naive e-mail address) is tacked onto the download request packet. In this scenario, peer D will reject the request. However, as mentioned previously, this solution does not maintain anonymity in the network since a unique identifier is tacked onto the message. Instead, we look at the second scenario where a download request is broadcast normally in the network. Peer D will send a download reply that contains the access control list, and she will not directly reject the request. Instead, peer B, the immediate neighbor to peer A, will check peer A's permissions and peer B will reject the request. This solution maintains anonymity, but at the moment it seems very easy to bypass the access control. We will research these ideas further during the course of the semester. During the course of this semester, we hope to extend these two ideas for access control, and perhaps devise a completely new method that has both strong access control and a strong notion of anonymity. Also, we will demonstrate our access control implementation in our demo application, Photoshare. We hope to distribute this program to the class during the course of the semester to gain interest in our project. Related Work A possible approach could be having a p2p framework with a language to model and reason about distributed authorization in open systems.Each peer in the framework has its own knowledge base of policy related information[1]. The high level behavior is determined by declarative event conditions, and the low level behavioris determined by the content of a peer's KB which includes local knowledge. The KB contains controls on what kind oif indormation can be sent out or received in messages. At the high level the language for KB and messages is similar to logic programs with open world semantics. P-Hera enables data owners to host data while considering security constraints at a fine-grained level. Furthermore, data can be searched and made available to users by considering the security constrains of CCs, DOs, and ROs. P-Hera is designed to address scalability and efficiency issues. It can be easily integrated with existing P2P infrastructures and in particular the ones based on supernodes[3]. supernodes, maintain indices of data contained in the nodes, as well as the access control policies of the nodes under their management. Query evaluator, content manager and policy manager are the components of a super node. In [2], trusted reference monitor (TRM) is introduced beyond the trusted hardware. By monitoring and verifying the integrity and properties of running applications in a platform using the functions of trusted computing, the TRM can enforce various policies on behalf of object owners. This architecture is extended to support user-based control policies, cooperating with existing services for user identity.[2] Timeline
Bibliography [1] PeerAccess: A Logic for Distributed Authorization-Winslett. Zhang, Bonatti. 12th ACM Conference on Computer and Communications Security, Nov 7-11, 2005. [2] Peer-to-Peer Access Control Architecture Using Trusted Computing Technology. Ravi Sandhu and Xinwen Zhang. 0th ACM Symposium on Access Control Models and Technologies (SACMAT), Stockholm, Sweden, June 1-3, 2005: 147-158. [3] P-Hera: Scalable fine-grained access control for P2P infrastructures.Bruno Crispo, Swaminathan Sivasubramanian, Pietro Mazzoleni.Parallel and Distributed Systems, 2005. Proceedings. 11th International Conference on Volume 1, 20-22 July 2005 Page(s):585 - 591 Vol. 1 [4] Zhang, X., Park, J., Parisi-Presicce, F., and Sandhu, A logical specification for usage control. In Proceedings of the Ninth ACM Symposium on Access Control Models and Technologies (Yorktown Heights, New York, USA, June 02 - 04, 2004). [5] Saunders, G., Hitchens, M., and Varadharajan, V. 2001. Role-based access control and the access control matrix. SIGOPS Oper. Syst. Rev. 35, 4 (Oct. 2001). [6] Pascal Fenkam, Schahram Dustdar, Engin Kirda, Gerald Reif, Harald Gall. Towards an Access Control System for Mobile Peer-to-Peer Collaborative Environments, wetice, 2002. [7] Park, J. S. and Hwang,Role-based access control for collaborative enterprise in peer-to-peer computing environments. In Proceedings of the Eighth ACM Symposium on Access Control Models and Technologies (Como, Italy, June 02 - 03, 2003). [8] M. Ripeanu, I. Foster, and A. Iamnitchi. Mapping the gnutella network: Properties of large-scale peer-to-peer systems and implications for system design. IEEE Internet Computing Journal, 6(1), 2002. [9] Jaeger, T., Edwards, A., and Zhang, X. Managing access control policies using access control spaces. In Proceedings of the Seventh ACM Symposium on Access Control Models and Technologies (Monterey,California, USA, June 03 - 04, 2002) |